| 일 | 월 | 화 | 수 | 목 | 금 | 토 |
|---|---|---|---|---|---|---|
| 1 | 2 | 3 | ||||
| 4 | 5 | 6 | 7 | 8 | 9 | 10 |
| 11 | 12 | 13 | 14 | 15 | 16 | 17 |
| 18 | 19 | 20 | 21 | 22 | 23 | 24 |
| 25 | 26 | 27 | 28 | 29 | 30 | 31 |
- 앱스토어
- SSL
- 인증
- 앱리소스
- MYSQL
- git
- SSH
- Android
- OTP
- Nodejs
- fido
- apple
- MSYS2
- SwiftUI
- openssl
- css
- 앨범북
- Xcode
- appres
- otpkey
- albumbook
- OSX
- 애플
- kmip
- SWIFT
- MFA
- WebAuthn
- FIDO2
- 안드로이드
- 2FA
- Today
- Total
인디노트
PKI:Public key infrastructure는 어떻게 동작할까? 본문
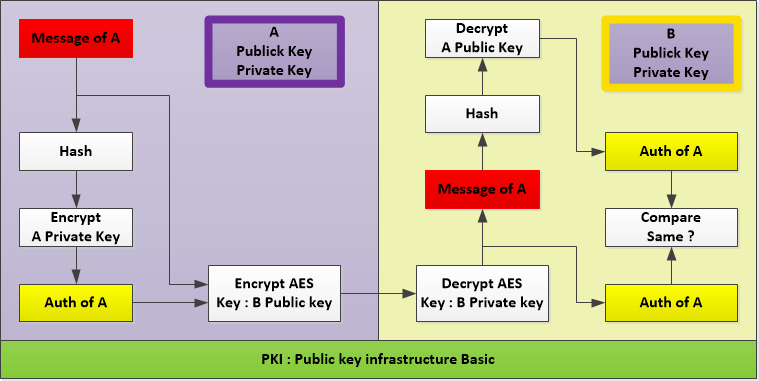
이해를 돕기 위해서 원 저자의 글에 컬러그림 한장을 추가했다. 원저자의 글은 맨아래 링크했다.
PKI는 어떻게 동작할까? ( Public key infrastructure )
참고
http://www.rebeladmin.com/2018/05/how-pki-works/
고객, 기술자와 이야기 할 때, 대부분의 사람들은 SSL이 " 더 안전 "하고 TCP 443 과 호환 된다는 것을 알고 있습니다. 그러나 대부분의 사람들은 인증서가 무엇인지,이 암호화 및 암호 해독이 어떻게 작동하는
지를 정확히 알지 못합니다. 그것이 어떻게 작동 하는
지를 아는 것은 매우 중요합니다. 그러면 배치와 관리가 쉬워집니다. 필자가 수행 한 PKI 관련 문제의 대부분은 서비스 수준 문제가 아니라 핵심 기술, 구성 요소 및 개념과 관련된 오해와 관련이 있습니다.
대칭 키 대 비대칭 키 : Symmetric-key vs Asymmetric-key
컴퓨터 세계에서 데이터를 암호화하는 데 사용하는 두 가지 유형의 암호화 방법이 있습니다. 대칭 방법은 문 자물쇠가 작동하는 것과 똑같은 방식으로 작동합니다. 문을 잠 그거나 열 수
있는 열쇠가 하나 있습니다. 공유 암호 및 개인 키 라고도
합니다. VPN 연결, 백업 소프트웨어는 대칭 키를 사용하여 데이터를 암호화하는 몇 가지 예입니다.
비대칭 키 방식은 다른 한편으로는 키 쌍을 사용 하여 암호화 및 암호 해독을 수행합니다. 하나는 공개 키 이고 다른 하나는 개인 키 입니다. 공개 키는 항상 공개 키로 배포되며 누구나 가질 수 있습니다. 개인 키는 개체에 대해 고유하며 다른 사람에게 배포되지 않습니다. 공개 키를 사용하여 암호화 된 메시지는 개인 키를 사용하여 해독 할 수 있습니다. 개인 키를 사용하여 암호화 된 메시지는 공개 키를 사용하여 암호를 해독 할 수 있습니다. PKI는 디지털 암호화 및 디지털 서명에 비대칭 키 방식을 사용합니다 .
디지털 암호화 : Digital Encryption
디지털 암호화는 양 당사자 간의 데이터 전송을 암호화하여 발신자가 예상 수신자에서만 열 수 있음을 의미합니다. 다른 권한이
없는 당사자조차도 암호화 된 데이터에 액세스 할 수 있기 때문에 데이터를 해독 할 수 없습니다. 그것을 설명하는 가장 좋은 방법은 다음과 같습니다.
우리
조직에는 Sean 이라는
직원이 있습니다. PKI 환경에서 그는 공개 키와 개인 키인 두 개의 키를 소유합니다. 그것은 암호화 및 서명 프로세스에 사용할 수 있습니다. 이제 그는 compony Account Manager Chris
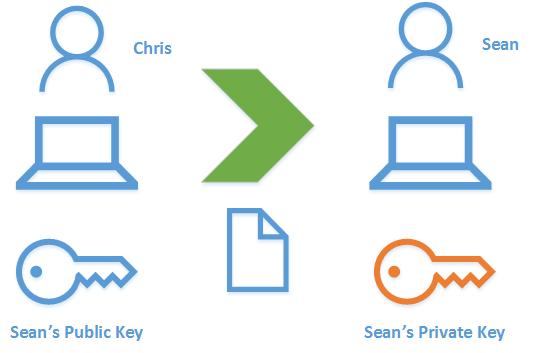
로부터 기밀 데이터 세트를 받도록 요구하고 있습니다. Sean 은 본인 외에는 누구도 이 기밀 데이터를 보여주고 싶어하지 않습니다. Chris가 Sean에게 보낼 데이터를 암호화하는 것이 가장 좋겠지요 ?
데이터를 암호화하기 위해 Sean은 공개 키를 Chris에게 보냅니다. 어떤 당사자에게 공개 키를 제공해도 아무런 문제가 없습니다. 그런 다음 Chris는 이 공개 키를 사용하여 Sean 에게 보내는 데이터를 암호화합니다. 이 암호화 된 데이터는 Sean의 개인 키로 만 열 수 있습니다. 그는 이 개인 키를 가지고 있는 유일한 사람입니다. 이것은 데이터에 대한 수신자와 그의 권한을 검증합니다.
전자 서명 : Digital Signature
디지털 서명은 서비스 또는 데이터의 진위 여부를 인증 ( authenticity ) 합니다. 이는 문서의 진위를 증명하기 ( prove its authenticity ) 위해 문서에 서명 ( 사인 : 우리나라로 보면 인감도장을 찍는 것 ) 하는 것과 유사 합니다.
예를 들어 amazon에서 구입하기 전에 디지털 인증서를 확인할 수 있으며 웹 사이트의 진위 여부를 확인하고 피싱 웹 사이트가 아닌 것으로 증명합니다. 유스 케이스로 더 살펴 보겠습니다. 이전 시나리오에서 Sean은 Chris로부터
받은 데이터를 성공적으로 해독했습니다.
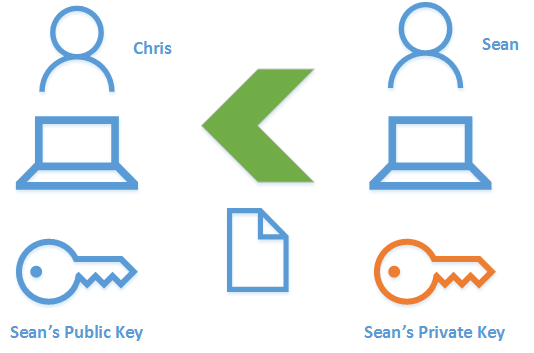
이제 Sean은 크리스에게 몇 가지 기밀 데이터를 보내고 싶어합니다. 크리스의 공개 키를 사용하여 동일한 방법으로 암호화할 수 있습니다. 하지만 문제는 크리스가 PKI 셋업의 일부가 아니며 키 쌍을 가지고 있지 않다는 것입니다. 크리스가 보낸 사람이 합법적인( legitimate) 지 그리고 그가 주장하는 동일한 사용자인지 확인하는 것이 꼭 필요합니다. Sean 이 디지털 서명을 사용하여 인증할 수 있고 크리스가 검증할 수 있다면 문제가 해결 됩니다.
이제 여기에서 Sean은 개인 키를 사용하여 데이터를 암호화합니다. 이제 해독 할 수 있는 유일한 열쇠는 Sean의 공개 키입니다. Chris는 이미 이 정보를 가지고 있습니다. 그는 공개 키를 가지고 있지 않더라도 공개 키를 배포 할 수 있습니다. Chris가 데이터를 수신하면 Sean의 공개 키를 사용하여 데이터를 암호 해독하고 보낸 사람이 Sean이라는 것을 확인합니다.
서명 및 암호화 : Signing and Encryption
이전 두 시나리오에서는 디지털 암호화 및 디지털 서명이 PKI와 함께 작동하는 방법을 설명했습니다. 그러나이 두 가지 시나리오를 함께 사용하면 암호화와 서명을 동시에 제공 할 수 있습니다. 해당 시스템을 수행하려면 두 가지 추가 기술을 사용하십시오.
대칭 키 : Symmetric-Key - 한 번 대칭 키는 비대칭 키 암호화 알고리즘보다 빠르기 때문에 메시지 암호화 프로세스에 사용합니다. 이 키는 수신자가 사용할 수 있어야하지만 수신자의 공개 키를 사용하여 여전히 암호화 된 보안을 향상시켜야합니다.
해싱 : Hashing - 서명 프로세스 동안 시스템은 원래 데이터를 나타 내기 위해 단방향 해시 값을 생성합니다. 심지어 일부 사용자는 해시 값을 가져 와서 원래 데이터를 얻기 위해
해시 하기 전 원래 값을 얻어낼 수 수 없습니다. 데이터에 대한 수정이 이루어지면 해시 값이 변경되고 수신자는 곧바로 알게
됩니다. 이러한 해싱 알고리즘은 암호화 알고리즘보다 빠르며 해시 된 데이터는 실제 데이터 값보다 작습니다.
시나리오를 기반으로 이것을 살펴 보겠습니다. 우리는 Simran과 Brian 두 명의 직원과 PKI 설정을 사용하는 두 명의 직원이 있습니다. 둘 다 개인 키와 공개 키가 할당되어 있습니다.
Simran은 암호화되고 서명 된 데이터 세그먼트를 Brian에게 보내려고 합니다. 프로세스는 주로 데이터 서명과 데이터 암호화의 두 단계로 나눌 수 있습니다. 데이터가 Brian에게 전송되기 전에 두 단계를 거치게 됩니다.
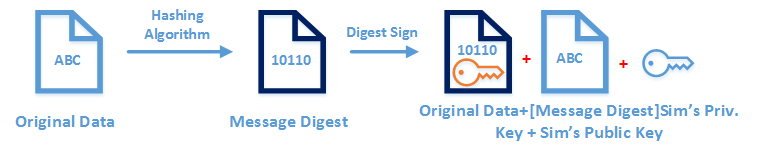
첫 번째 단계는 데이터 세그먼트에 서명 ( signed data) 하는 것입니다. 시스템은 Simran 으로 부터 데이터를 수신하고 첫 번째 단계는 해싱 알고리즘을 사용하여 메시지 다이제스트를 ( message digest ) 생성하는 것입니다. 이렇게 하면 데이터 무결성이 보장 ( ensure data integrity ) 되고 일단 발신자 시스템을 떠난 후에 변경되면 수신자는 해독 ( decryption process ) 프로세스를 사용하여 쉽게 식별 할 수 있습니다. 이것은 단방향 프로세스입니다. 메시지 다이제스트가 생성되면 다음 단계에서 메시지 요약을 Simran 의 개인 키를 사용하여 암호화하여 디지털 서명합니다. Brian은 메시지의 진위 여부를 해독하고 확인할 수 있도록 Simran의 공개 키도 포함합니다. 일단 프로세스가 암호화 ( encrypt ) 되면 원래의 데이터 값이 첨부됩니다. 이 프로세스로 인해 데이터가 변경되지 않고 정확한 발신자 (Genuine) 로 부터 전송됩니다.
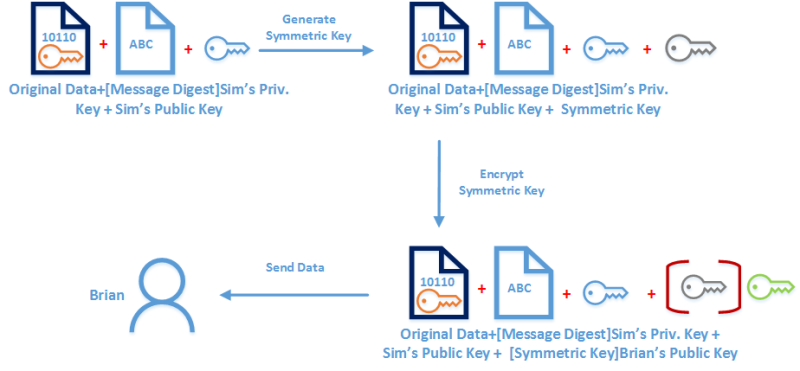
작업의 다음 단계는 데이터를 암호화하는 것입니다. 첫 번째 단계는 데이터를 암호화하기 위해 한 번 대칭 키를 생성하는 것입니다. 비대칭 알고리즘은 긴 데이터 세그먼트와 함께 사용하는 대칭 알고리즘과 비교하여 효율성이 떨어집니다. ( 암복호 속도 1,000배 차이 )
대칭 키가 생성되면 데이터를 사용하여 암호화됩니다 (메시지 다이제스트, 서명 포함). 이 대칭 키는 Brian에서 메시지의 암호를 해독하는 데 사용됩니다. 브라이언에 대해서만 사용할 수 있도록 해야 합니다. 가장 좋은 방법은 Brian의 공개 키를 사용하여 대칭 키를 암호화하는 것입니다. 따라서 일단 암호를 받으면 개인 키를 사용하여 암호를 해독 할 수 있게 됩니다. 이 프로세스는 대칭 키 자체 만 암호화하므로 나머지 메시지는 그대로 유지됩니다. 완료되면 데이터를 브라이언에게 보낼 수 있습니다.
다음 단계에서는 Brian 측에서 해독 프로세스가 어떻게 수행되는지 살펴 봅니다.
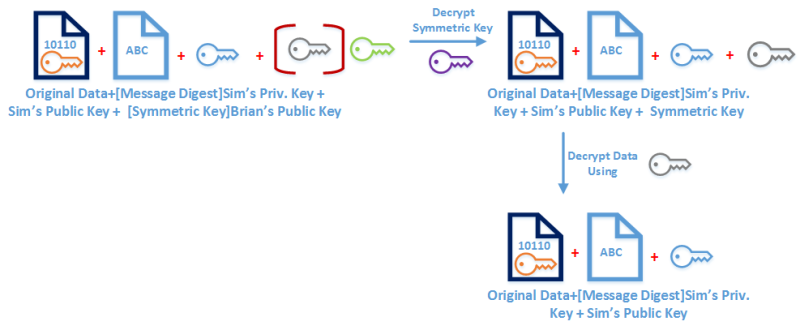
메시지 암호 해독 프로세스는 대칭 키를 해독하는 것으로 시작됩니다. Brian은 암호 해독 프로세스를 진행하기 위해 대칭키가 필요합니다. Brian의 개인 키를 사용하여 해독 할 수 있습니다. 복호화가 끝나면 대칭 키를 사용하여 메시징 된 다이제스트 + 서명을 해독 할 수 있습니다. 암호 해독이 완료되면 동일한 키 정보를 사용하여 유사한 메시지를 한 번만의 키로 해독 할 수 없습니다.
이해를 돕기 위해서 원 저자의 글에 컬러그림 한장을 추가했다. 원저자의 글은 맨아래 링크했다.
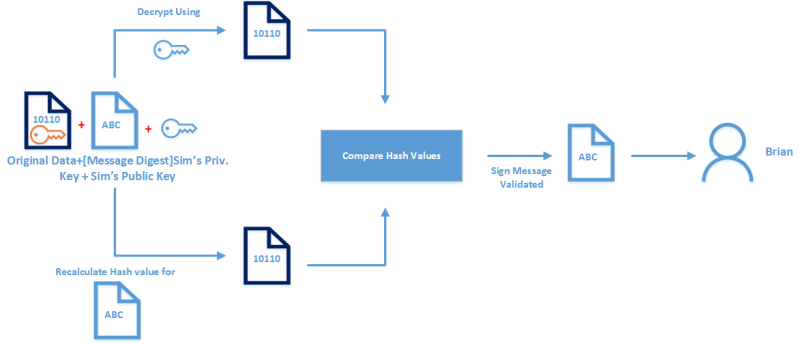
이제 우리는 해독 된 데이터를 가지고 다음 단계는 서명을 검증하는 것입니다. 이 시점에서 우리는 Simran의 개인 키를 사용하여 암호화 된 메시지 다이제스트를 갖게됩니다.
암호화 된 메시지에 첨부 된 Simran의 공개 키를 사용하여 해독 할 수 있습니다. 복호화가 끝나면 메시지 다이제스트를 가져올 수 있습니다. 이 다이제스트 값은 단방향 ( one-way ) 입니다. 우리는 반대로 결과값을 가지고 원래의 데이터를 절대 얻을 수 없습니다.
검색된 원래 데이터 다이제스트 값은 보낸 사람이 사용한 알고리즘과 정확히 동일한 알고리즘을 사용하여 다시 계산됩니다. 그런 다음 새로 생성 된 다이제스트 값이 메시지에 첨부 된 다이제스트 값과 비교됩니다. 값이 같으면 통신 프로세스 중에 데이터가 수정되지 않았음을 확인할
수 있습니다. 가치가 동일하면 서명이 확인되고 원래 데이터가 Brian
에게 전달됩니다. 다이제스트 값이 다른 경우 메시지가 변경되었거나 Simran 이 서명하지 않아 메시지가 삭제됩니다.
PKI 환경이 암호화 / 암호 해독 프로세스 및 디지털 서명 / 검증 프로세스와 함께 어떻게 작동하는지 설명했습니다.
질문이 있으시면 rebeladm@live.com에 저에게 연락 해주십시오. 또한 새 블로그 게시물에 대한 업데이트를 받으려면 twitter @rebeladm 에서 저를 따라 오십시오 .
Refer & Translation
http://www.rebeladmin.com/2018/05/how-pki-works/
How PKI Works ?
MAY 13, 2018 BY DISHAN M. FRANCIS 1 COMMENT
When I talk to customers, engineers, most of them know SSL is “more secure” and works with TCP 443.
But most of them do not really know what is a certificate and how this
encryption and decryption works. It is very important to know how it’s
exactly works then the deployment and management becomes easy. Most of
the PKI related issues I have worked on are related to misunderstanding
on core technologies, components and concepts related to it, rather than
service level issues.
Symmetric-key vs Asymmetric-key
There
are two type of cryptographic methods use to encrypt the data in
computer world. Symmetric method works exactly the same way your door
lock works. You have one key to lock or open the door. This is also
called as shared secret and private key. VPN connections, Backup
Software are some of the examples where still uses Symmetric-key to
encrypt data.
Asymmetric-key method is in other hand uses key pair to do the encryption and decryption. It includes two keys one is public key and the other one is private key.
Public key is always distributed to public and any one can have it.
Private key is unique for the object and it will not distribute to
others. Any message encrypts using a public key only can decrypt using
its private key. Any message encrypts using private key only can decrypt
using public key. PKI uses the Asymmetric-key method for digital encryption and digital signature.
Digital Encryption
Digital
encryption mean, the data transfer between two parties will be
encrypted and sender will ensure it only can open from the expected
receiver. Even another unauthorized party gain access to that encrypted
data, they will not be able to decrypt the data. Best way to explain it
will following example,
We have an employee in organization called Sean. In PKI environment, he owns two keys which is public key and private key. It can use to encryption and signature process. Now he has a requirement to receive set of confidential data from compony account manager Chris. He doesn’t want anyone else to have this confidential data. The best way to do this to encrypt the data which going to send from Chris to Sean.
In
order to encrypt the data, Sean sends his public key to Chris. There is
no issue with providing public key to any party. Then Chris uses this
public key to encrypt the data he is sending over to Sean. This
encrypted data only can open using Sean’s private key. He is the only
one have this private key. This verifies the receiver and his authority
over the data.
Digital Signature
Digital
signature verifies the authenticity of the service or data. It is
similar to signing a document to prove its authenticity. As an example,
before purchase anything from amazon, we can check its digital
certificate and it will verify the authenticity of the website and prove
it’s not a phishing website. Let’s look in to it further with a use
case. In previous scenario, Sean successfully decrypted the data he
received from Chris. Now Sean wants to send some confidential data back
to Chris. It can be encrypt using same method using Chris’s public key.
But issue is Chris is not part of the PKI setup and he do not have key
pair. Only thing Chris need to verify the sender is legitimate and its
same user he claims to be. If Sean can certify it using digital
signature and if Chris can verify it, the problem is solved.
Now
in here, Sean encrypt the data using his private key. Now the only key
it can be decrypt is the Sean’s public key. Chris already have this
information. Even if he doesn’t have public key it can distribute to
him. When Chris receives the data, he decrypts it using Sean’s public
key and it confirms the sender is definitely Sean.
Signing and Encryption
In
previous two scenarios, I have explained how digital encryption and
digital signature works with PKI. But both of these scenarios can
combined together to provide the encryption and signing in same time. In
order to do that system, use two additional techniques.
Symmetric-Key –
One time symmetric-key will use for the message encryption process as
it is faster than the asymmetric-key encryption algorithms. This key
need to be available for the receiver but to improve the security it
will be still encrypt using receiver’s public key.
Hashing –
During the sign process system will generate a one-way hash value to
represent the original data. Even some one manage to get that hash value
it will not possible to reverse engineer to get the original data. If
any modification done to the data, hash value will get change and the
receiver will know straight away. These hashing algorithms are faster
than encryption algorithms and also the hashed data will be smaller than
actual data values.
Let’s
look in to this based on a scenario. We have two employees Simran and
Brian and both using PKI setup. Both have their private and public keys
assigned.
Simran wants to send encrypted and signed data segment to Brian. Process mainly can be divided in to two stages which is data signing and data encryption. It will go through both stages before the data send to Brian.
The first stage is to sign the data segment. System received the Data from Simran and first step is to generate the message digest using the hashing algorithms. This will ensure data integrity and if its altered once it leaves the senders system, receiver can easily identify it using the decryption process. This is one-way process. Once message digest it generated, in next step the messages digest will encrypt using Simran’s Private key in order to digitally sign. It will also include Simran’s Public key so Brian will be able to decrypt and verify the authenticity of the message. Once encrypt process finish it will attached with original data value. This process will ensue data was not altered and send from exact expected sender (Genuine).
Next
stage of the operation is to encrypt the data. First step is in the
process is to generate one time symmetric key to encrypt the data.
Asymmetric algorithm is less efficient compare to symmetric algorithms
to use with long data segments. Once symmetric key is generated the data
will encrypt using it (including message digest, signature). This
symmetric key will be used by Brian to decrypt the message. There for we
need to ensure it only available for Brian. The best way to do it is to
encrypt the symmetric key using Brian’s public key. So, once he
received it, he will be able to decrypt using his private key. This
process is only encrypting symmetric key itself and rest of the message
will stay same. Once it completed the data can send to Brian.
Next step of the process to see how the decryption process will happen on Brian’s side.
Message decryption process starts with decrypting the symmetric key. Brian needs symmetric to go further with decryption process. It only can decrypt using Brian’s private key. Once its decrypt, symmetric key can use to decrypt the messaged digests + signature. Once decryption done same key information cannot be used to decrypt similar messages as its one time key.
Now
we have the decrypted data and next step is to verify the signature. At
this point we have message digest which is encrypt using Simran’s
private key. It can be decrypt using Simran’s public key which is
attached to the encrypted message. Once its decrypt we can retrieve the
message digest. This digest value is one-way. We cannot reverse engineer
it. There for retrieved original data digest value will recalculate
using exact same algorithm used by sender. After that this newly
generated digest value will compare with the digest value attached to
message. If the value is equal it will confirm the data wasn’t modified
during the communication process. When value is equal, signature will be
verified and original data will issue to Brain. If the digest values
are different the message will be discard as it been altered or not
signed by Simran.
This explained how PKI environment works with encryption/decryption process as well as digital signing /verification process.
If you have any questions feel free to contact me on rebeladm@live.com also follow me on twitter @rebeladm to get updates about new blog posts.
'인증기술 > PKI 기술' 카테고리의 다른 글
| OpenSSL API를 이용한 보안 프로그래밍, Part 2: 안전한 핸드쉐이크(handshake) (한글) (0) | 2018.10.08 |
|---|---|
| OpenSSL API를 이용한 보안 프로그래밍, Part 1: API의 개요 (한글) (0) | 2018.10.08 |
| [OpenSSL] 마소연재 강좌 (0) | 2018.10.05 |
| [OpenSSL] API를 이용한 보안 프로그래밍 (0) | 2018.10.05 |
| JAVA에서의 AES 암호화 및 복호화 (0) | 2018.10.05 |